Top Stories
New Scheme Boosts Secure Neural Network Inference Efficiency
BREAKING: A groundbreaking study from the School of Cyber Science and Engineering at Southeast University and Purple Mountain Laboratories has just revealed an innovative scheme for secure neural network inference, addressing urgent privacy concerns that have emerged in the age of cloud computing. The research, titled “Efficient Privacy-Preserving Scheme for Secure Neural Network Inference“, proposes a robust solution to protect sensitive user data and cloud-stored intelligent model parameters.
As reliance on cloud services grows, the risk of sensitive data transmission in plaintext raises significant privacy and security alarms. Users are increasingly vulnerable to unauthorized access as cloud servers handle their private information. The new scheme aims to ensure that both user data and server models are safeguarded, enabling fast and accurate inference, which is crucial for modern applications.
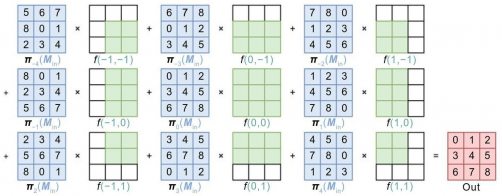
This innovative approach employs homomorphic encryption and secure multi-party computation to create a privacy-preserving environment. The researchers optimized the inference process through three key designs:
1. **Dividing inference into three stages** (merging, preprocessing, and online) to streamline operations.
2. **Introducing a network parameter merging approach** to minimize multiplication levels and reduce ciphertext-plaintext operations.
3. **Developing a fast convolution algorithm** to enhance computational efficiency.
The study leverages the CKKS homomorphic encryption algorithm, allowing for high-precision floating-point computations. By merging consecutive linear layers, the scheme reduces communication rounds and costs, transforming convolutional operations into matrix-vector multiplications to fully utilize ciphertext “slots.”
Extensive experiments validate the effectiveness of this scheme, achieving an impressive 99.24% inference accuracy on the MNIST dataset and 90.26% accuracy on the Fashion-MNIST dataset. Compared to leading methods like DELPHI, GAZELLE, and CryptoNets, this new scheme reduces online-stage linear operation time by at least 11%, cuts computational time by approximately 48%, and decreases communication overhead by 66% versus non-merging approaches. These enhancements are crucial for industries relying on rapid and secure data processing.
The paper is authored by a team of experts: Liquan CHEN, Zixuan YANG, Peng ZHANG, and Yang MA. Their findings are expected to have a profound impact on cloud computing security protocols.
As cloud services continue to expand, this research represents a pivotal advancement in ensuring user privacy while maintaining operational efficiency. The full text of the study is available at https://doi.org/10.1631/FITEE.2400371.
Stay tuned for more updates on this developing story, as the implications of this research could reshape the future of data security in cloud environments.
-

 World2 weeks ago
World2 weeks agoGlobal Air Forces Ranked by Annual Defense Budgets in 2025
-

 World2 weeks ago
World2 weeks agoMass Production of F-35 Fighter Jet Drives Down Costs
-

 Top Stories2 weeks ago
Top Stories2 weeks agoNew ‘Star Trek: Voyager’ Game Demo Released, Players Test Limits
-

 Top Stories2 weeks ago
Top Stories2 weeks agoDirecTV to Launch AI-Driven Ads with User Likenesses in 2026
-

 Science2 weeks ago
Science2 weeks agoTime Crystals Revolutionize Quantum Computing Potential
-
 World2 weeks ago
World2 weeks agoElectrification Challenges Demand Advanced Multiphysics Modeling
-

 Lifestyle2 weeks ago
Lifestyle2 weeks agoLia Thomas Honored with ‘Voice of Inspiration’ Award at Dodgers Event
-

 Entertainment2 weeks ago
Entertainment2 weeks agoFreeport Art Gallery Transforms Waste into Creative Masterpieces
-

 Lifestyle2 weeks ago
Lifestyle2 weeks agoDiscover Reese Witherspoon’s Chic Dining Room Style for Under $25
-

 Health2 weeks ago
Health2 weeks agoGavin Newsom Critiques Trump’s Health and National Guard Plans
-

 Entertainment2 weeks ago
Entertainment2 weeks agoFast & Furious Coaster Hits the Track at Universal Studios
-

 Science2 weeks ago
Science2 weeks agoWaning Crescent Moon: What to Expect on October 17